ASP.Net Core Interview Questions and Answers - Part 04
Are you preparing for the .Net Core Interview? If yes, then you are at the right place. This is the ASP.Net Core Interview Questions and Answers article series. Here we will see the Top 150+ .Net Core Interview Questions with Answers.
Please visit our YouTube Channel for Interviews and other videos by below link:
Please read the complete Design Pattern, C#, MVC, WebAPI, and .Net Framework Interview Questions and Answers article series here.
Introduction
This is the 4th part of the .Net Core Interview Questions and Answers article series. Each part contains ten .Net Core Interview Questions. Please read all the .Net Interview Questions list here.
I will highly recommend to please read the previous parts over here before continuing the current part:
ASP.Net Core Interview Questions and Answers - Part 04
Q033. What is Blazor? What are the advantages of Blazor?
Blazor is a free and open-source web framework developed by Microsoft that enables developers to create web apps using C# and HTML. Blazor is Microsoft’s latest web framework technology for building interactive client-side web UI with .NET.
It is a new framework introduced with .Net Core 3.0. We generally use the C# code on the server side only, but with Blazor we can use C# code on the client side as well.
Blazor lets you build interactive web UIs using C# instead of JavaScript. Blazor apps are composed of reusable web UI components implemented using C#, HTML, and CSS. Both client and server code is written in C#, allowing you to share code and libraries.
Use of Blazor: With Blazor you can:
- Create rich interactive UIs using C# instead of JavaScript
- Share server-side and client-side app logic written in .NET.
- Render the UI as HTML and CSS for wide browser support, including mobile browsers.
- Integrate with modern hosting platforms, such as Docker.
- Build hybrid desktop and mobile apps with .NET and Blazor.
Blazor apps are based on components. A component in Blazor is an element of UI, such as a page, dialog, or data entry form. Components are .NET C# classes built into .NET assemblies that define flexible UI rendering logic or Handle user events.
Advantages of .Net in Blazor for Client-Side Web Development:
- Write code in C# instead of JavaScript.
- Leverage the existing .NET ecosystem of .NET libraries.
- Benefit from .NET's performance, reliability, and security.
- Share app logic across server and client.
- Stay productive on Windows, Linux, or macOS with a development environment, such as Visual Studio or Visual Studio Code.
 |
| Source: Microsoft Doc |
With the release of .NET 5, Blazor has stopped working on Internet Explorer and the legacy version of Microsoft Edge.
Q034. What is the difference between Blazor Server and Blazor WebAssembly?
There are five different editions of Blazor apps have been announced - Blazor Server, Blazor WebAssembly, Blazor PWA, Blazor Hybrid, and Blazor Native.
Blazor Server and Blazor WebAssembly have several differences. Blazor WebAssembly is also known as Blazor Wasm.
Blazor Server:
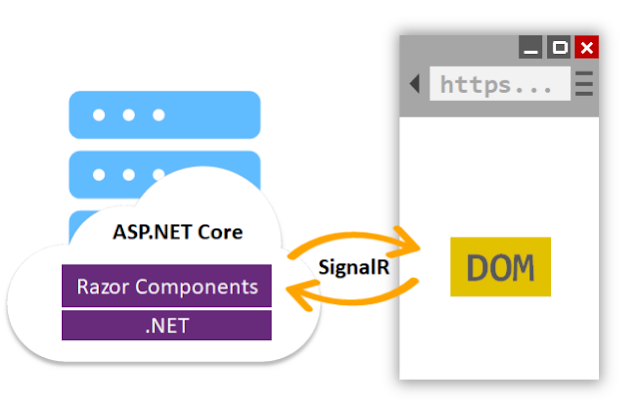
Blazor Server provides support for hosting Razor components on the server in an ASP.NET Core app. UI updates are handled over a SignalR connection. Blazor Server was released as a part of .NET Core 3. Blazor Server uses ASP.Net Core application and we can use entity framework to connect with SQL Databases.
Blazor Server apps render content differently than traditional models for rendering UI in ASP.NET Core apps using Razor views or Razor Pages. Blazor Server produces a graph of components to display similar to an HTML or XML DOM.
The component graph includes states held in properties and fields. Blazor evaluates the component graph to produce a binary representation of the markup, which is sent to the client for rendering.
When an update occurs, the component graph is rerendered, and a UI diff (difference) is calculated. This diff is the smallest set of DOM edits required to update the UI on the client. The diff is sent to the client in a binary format and applied by the browser.
Blazor WebAssembly (Blazor Wasm):
Blazor WebAssembly is a single-page app (SPA) framework for building interactive client-side web apps with .NET. Blazor WebAssembly uses open web standards without plugins or recompiling code into other languages. Blazor WebAssembly works in all modern web browsers, including mobile browsers. Blazor Wasm works on the browser and downloads the Blazor application on the client side.
Running .NET code inside web browsers is made possible by WebAssembly (wasm). WebAssembly is a compact bytecode format optimized for fast download and maximum execution speed. WebAssembly is an open web standard and is supported in web browsers without plugins.
WebAssembly code can access the full functionality of the browser via JavaScript, called JavaScript interoperability, often shortened to JavaScript interop or JS interop. .NET code executed via WebAssembly in the browser runs in the browser's JavaScript sandbox with the protections that the sandbox provides against malicious actions on the client machine.
Single-page apps that are downloaded to the client's web browser before running. The size of the download is larger than for Blazor Server, depending on the app, and the processing is entirely done on the client's hardware. However, this app type enjoys rapid response time. As its name suggests, this client-side framework is written in WebAssembly, as opposed to JavaScript (while they can be used together).
Blazor PWA supports progressive web apps (PWA) and Blazor Hybrid is a platform-native framework but still renders the user interface using web technologies. Blazor Hybrid is in preview and not recommended for production workloads.
Blazor Native is a platform-native framework that renders a platform-native user interface. It has also been considered but has not reached the planning stage yet.
Q035. What is the use of the UseDeveloperExceptionPage() in .Net Core?
The UseDeveloperExceptionPage() method belongs to the Microsoft.AspNetCore.Builder namespace of UseDeveloperExceptionPage Extensions static class.
The purpose of this function is to capture synchronous and asynchronous System.Exception instances from the pipeline and generates HTML error responses.
It returns a reference to the app after the operation is completed. We use the UseDeveloperException() extension method to render the exception during the development mode.
This should only be enabled in the Development environment because detailed exception information shouldn't be displayed publicly when the app runs in the Production environment.
If you want your application to display a page that shows detailed information about the unhandled exception, then you need to configure the Developer Exception Page middleware in the request processing pipeline. To do so, modify the Configure() method of the Startup class:
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
}
We need to configure the UseDeveloperExceptionPage() Middleware as early as possible in the application’s request processing pipeline so that it can handle the unhandled exception and then display the Developer Exception Page with detailed information about the exception.
The Developer Exception Page displays detailed information about unhandled request exceptions. ASP.NET Core apps enable the developer exception page by default when running in the Development environment.
The developer exception page runs early in the middleware pipeline so that it can catch unhandled exceptions thrown in the middleware that follows. The Developer Exception Page can include the following information about the exception and the request:
- Stack trace
- Query string parameters, if any
- Cookies, if any
- Headers
The Developer Exception Page isn't guaranteed to provide any information, so please use Logging for complete error information.
Q036. What is Transfer-Encoding in .Net Core?
Transfer encoding is used to transfer the entity to the user. It is set to Chunked indicating that Chunked transfer encoding data transfer mechanism of the HTTP Protocol is initiated in which data is sent in a series of "chunks".
The HttpResponseHeaders.TransferEncodingChunked Property is used to Get or Set a value that indicates if the Transfer-Encoding header for an HTTP response contains chunked. It is true if the Transfer-Encoding header contains chunked, otherwise false.
Basically, ASP.NET Core HttpClient sends requests chunked by default. This was not the case for .NET Framework. This can cause some issues with compatibility.
ASP.NET transfers the data to the client in chunked encoding (Transfer-Encoding: chunked), if you prematurely flush the Response stream for the HTTP request and the Content-Length header for the Response is not explicitly set by you. You need to explicitly set the Content-Length header for the Response to prevent ASP.NET from chunking the response on flushing.
Q037. What is ASP.Net Core Identity?
ASP.NET Core Identity is an API that supports user interface (UI) login functionality. It manages users, passwords, profile data, roles, claims, tokens, email confirmation, and more.
ASP.Net Core Identity provides a wide range of helper functions to perform essential core features related to user identity management.
Users can create an account with the login information stored in Identity or they can use an external login provider like Facebook, Google, Microsoft Account, and Twitter.
Identity is typically configured using a SQL Server database to store user names, passwords, and profile data. Alternatively, another persistent store can be used, for example, Azure Table Storage. ASP.NET Core Identity adds user interface (UI) login functionality to ASP.NET Core web apps.
ASP.NET Core Identity is a membership system that adds user registration and login capabilities to an ASP.NET Core web UI. The membership system handles both authentication and authorization concerns.
Authentication is concerned with who you are. Authorization is concerned with what you're allowed to do. Authentication is therefore a prerequisite for authorization.
Q038. What is the difference between Stateful and Stateless authentication in .Net Core?
Stateful Authentication or Session-Based Authentication:
Stateful Authentication is a way to verify a user by having the server or backend store session information, such as user properties.
Stateful authentication is also called session-based authentication or cookie-based authentication for the session information the server must store on the user.
After successful authentication, the application generates a random token to send back to the client and then creates a client-authenticated session in memory or an internal database.
When a client tries to access the application with a given token, the application tries to retrieve session data from session storage, checks if the session is valid and then decides whether the client has access to the desired resource or not.
It is simpler to implement than Stateless or Token-Based Authentication but it is resource-intensive causing the server to perform lookups for every request. Stateful authentication is straightforward and easy to implement however its drawbacks include a lack of scalability.
Stateless Authentication or Token Based Authentication:
Stateless Authentication is a way to verify users by having much of the session information such as user properties stored on the client side. Stateless authentication is efficient, scalable, and interoperable.
Stateless authentication uses tokens, most often a JSON Web Token (JWT) or OpenID Connect, that contain the user and client information. A popular form of stateless or token-based authentication is Security Assertion Markup Language (SAML) as well.
After successful authentication, the application generates a token with all necessary data, signs it with a public key, and sends it back to a client. There is a standard for token generation, it is JWT (JSON Web Token).
When a client tries to access the application with a token, the application verifies the token sign with a private key, checks if the token is expired, retrieves all session data from the token, and makes a decision if a client has access to the desired resource.
Stateless authentication stores the user session data on the client-side (browser). Since the user session is stored on the client side, the server only has to verify its validity by checking whether the payload and the signature match.
Stateful Authentication vs Stateless Authentication:
In stateful authentication, it is impossible to steal session information from the session identifier because it is just an identifier associated with the session. But in Stateless authentication Session identifier contains all authentication information and it is possible to steal sensitive information, it is not encrypted.
In stateful authentication, it is possible to revoke a session at any time but it is not possible in stateless authentication since the session token contains an expiration date, it is impossible to revoke the authentication session.
In stateful authentication, it is possible to modify any session data in session data storage. But it is not possible in stateless authentication because the session token contains all session data, it is not possible to modify it.
In stateful authentication when retrieving session information, the service always gets access to session storage which causes additional resource consumption. But this is not the case for stateless as the session identifier contains all session information.
When stateful session information is stored in an external database, there is a need to implement session database persistence. In the case of a stateless since the Session identifier contains all session information, there is no need to implement additional functionality.
In stateful authentication the authentication token is just an identifier, so session data does not affect its size. But in stateless authentication, if an authentication session contains a large amount of data, the authentication token also becomes large, which can cause additional load on a network.
In stateful authentication, only the authentication system is able to retrieve session information from an authentication token, so there are no more vulnerabilities. But in other cases to decrypt session information from a token, all parts of the system should share the same key. And, if at least one system is compromised, all parts of the system are under the threat.
Q039. What is the difference between OpenID, OAuth, and SAML?
OAuth vs OpenID vs SAML:
OAuth 2.0 is a framework that controls authorization to a protected resource such as an application or a set of files, while OpenID Connect and SAML are both industry standards for federated authentication.
Using either OpenID Connect or SAML independently, enterprises can achieve user authentication and deploy single sign-on. Though they both deal with logins, they have different strengths and weaknesses.
The OpenID is used for authentication while OAuth is used for authorization.
OpenID Connect is built on top of OAuth 2.0 protocol and uses an additional JSON Web Token (JWT), called an ID token, to standardize areas that OAuth 2.0 leaves up to choices, such as scopes and endpoint discovery. It is specifically focused on user authentication and is widely used to enable user logins on consumer websites and mobile apps.
On the other hand, SAML is independent of OAuth, relying on an exchange of messages to authenticate in XML SAML format, as opposed to JWT. It is more commonly used to help enterprise users sign in to multiple applications using a single login.
OpenID was created for federated authentication, meaning that it lets a third-party application authenticate users for you using accounts that you already have. In contrast, OAuth was created to remove the need for users to share their passwords with third-party applications.
OAuth:
The OAuth provides secure delegated access. An application can take action or access resources from a server on behalf of the user, without them having to share their credentials.
It does this by allowing the identity provider (IdP) to issue tokens to third-party applications with the user’s approval.
For example when you ever signed up to a new application and agreed to let it automatically source (import) new contacts via Facebook or your phone contacts. So OAuth is an open standard for access delegation deals with authorization
The OAuth 2.0 protocol provides API security through scoped access tokens. OAuth 2.0 enables you to delegate authorization, while OIDC enables you to retrieve and store authentication information about your end-users. OIDC extends OAuth 2.0 by providing user authentication and single sign-on (SSO) functionality.
OpenID Connect(OIDC):
OpenID Connect is an open standard that organizations use to authenticate users. IdPs use this so that users can sign in to the IdP, and then access other websites and apps without having to log in or share their sign-in information.
For example using a Google account to sign in to applications like YouTube, Facebook, or any online shopping cart website to log into.
The OpenID Connect is an authentication standard built on top of OAuth 2.0. It adds an additional token called an ID token.
When a client uses OAuth, a server issues an access token to a third party, the token is used to access a protected resource, and the source validates the token. Notice, that at no point is the identity of the owner of the token verified.
SAML(Security Assertion Markup Language):
SAML is an XML-based standard for exchanging authentication and authorization data between IdPs and service providers to verify the user’s identity and permissions, then grant or deny their access to services.
SAML authentication is used in the work environment. For example, it enables you to log into your corporate intranet or IdP and then access numerous additional services, such as Salesforce, Box, or Workday, without having to re-enter your credentials.
Q040. What is the Ok() helper method in ASP.NET Core?
Ok helper method return Status 200 OK response. This status code is returned when requested data is found. If you want you can return the data as well like Ok(object).
It is defined in Microsoft.AspNetCore.Mvc namespace.
Q041. What is NotFound() helper method in ASP.NET Core?
NotFound() helper method return Status 404 NotFound response. This status code return when requested data is not found.
You can also use NotFound(object) which creates a NotFound ObjectResult that produces a Status404NotFound response.
It is also defined in Microsoft.AspNetCore.Mvc namespace.
Q042. What is BadRequest() helper method in ASP.NET Core?
BadRequest() helper method return Status 400 BadRequest response. This status code returned when data provided in the request failed the validation.
You can also use BadRequest(ModelStateDictionary) which creates an BadRequestObjectResult that produces a Status400BadRequest response and BadRequest(Object) which creates an BadRequestObjectResult that produces a Status400BadRequest response.
It is also defined in Microsoft.AspNetCore.Mvc namespace.
To Be Continued Part-05...
Recommended Articles
Thanks for visiting this page. Please follow and join us on LinkedIn, Facebook, Telegram, Quora, YouTube, Twitter, Pinterest, Tumbler, and VK for regular updates.












I was surfing net and fortunately came across this site and found very interesting stuff here. Its really fun to read. I enjoyed a lot. Thanks for sharing this wonderful information.
ReplyDeletecolumbus web design agency